Day 4 - ClamAV
Writer: Niklas Saari - OUSPG / University of Oulu
Brief history of ClamAV
The struggle is real between the malware developers and the developers of the anti-malware-things. If you are not professional researcher, or not having time for making specific research for all your mysterious files, (or just lacking the required knowledge) you eventually might need some automated solution for classifying whether your files are safe or not.
Many commercial anti-malware "solutions" exists, and have been developed in the past, now, and probably will be developed in the future as well, as there will always be this endless cat-and-mouse game. Not everyone are willing to use commercial products, and shared knowledge can be though as power, when aiming for open source projects instead.
ClamAV is one of the few available open source antivirus engines. It really takes a lot of effort to maintain database of millions different kind of malware identification rules - for years as the ClamAV was introduced first time in 2001, yet it is still actively maintained and databases are updated.
The creator of ClamAV - Tomasz Kojm had encountered malware named as "FunLove" in the 2000s, because this was causing some troubles for his friends in the Internet café. "FunLove", which might be better known as the virus that Warner Brothers shipped with the Powerpuff Girls DVD[1] (which eventually had to be recalled) many years ago, might be considered as inspiration for Kojm, as he found researching of it fascinating. This and the "weak usability" of the first open source AV product OpenAntiVirus made Kojm to start his own project. [2]
The purpose of ClamAV was originally to be especially designed for scanning emails in mail gateways[3], but nowadays it is general purpose malware scanner.
Big thanks for Tomasz Kojm and other ClamAV contributors in past years!
See the project homepage: https://www.clamav.net/
Running ClamAV in Docker container
Sometimes there are cases, where one does not want to install whole anti-virus software for their system, but is still wanting to have some sample(s) to be analysed against ClamAV database.
Here, in the CinCan project we have been dockerizing many tools, and ClamAV is one of them.
With Docker, it is possible to scan given directory or file(s) without letting the antivirus software accessing for whole system.
Basic usage
For helping with usage of different kind containers - cincan tool wrapper has been created. Tool should be installed before following examples can be used.
To use ClamAV to scan single file with cincan tool, following command can be used:
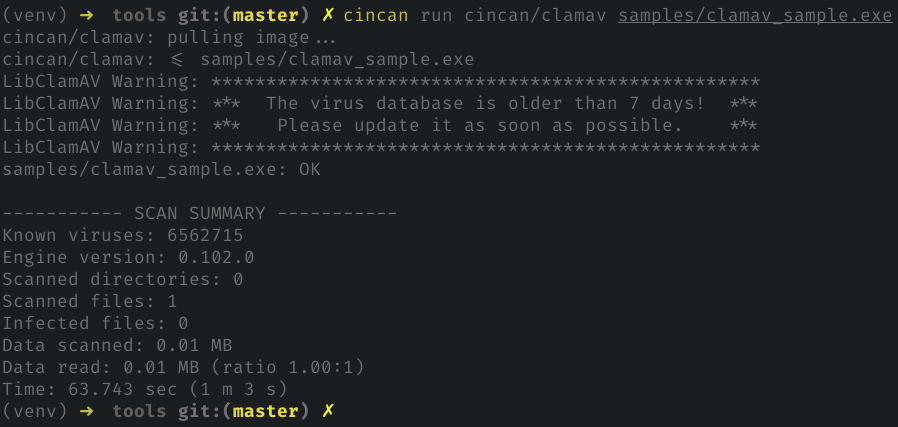
cincan run cincan/clamav samples/clamav_sample.exe
Docker container is using the 'clamscan' client of the ClamAV, and initialization takes time as it loads up databases - it is recommended to run as many files as possible at once to speed up process. In this case database is outdated, but later we show how you can update the database of container!
Analysing provides these kind of results for non-malicious results:
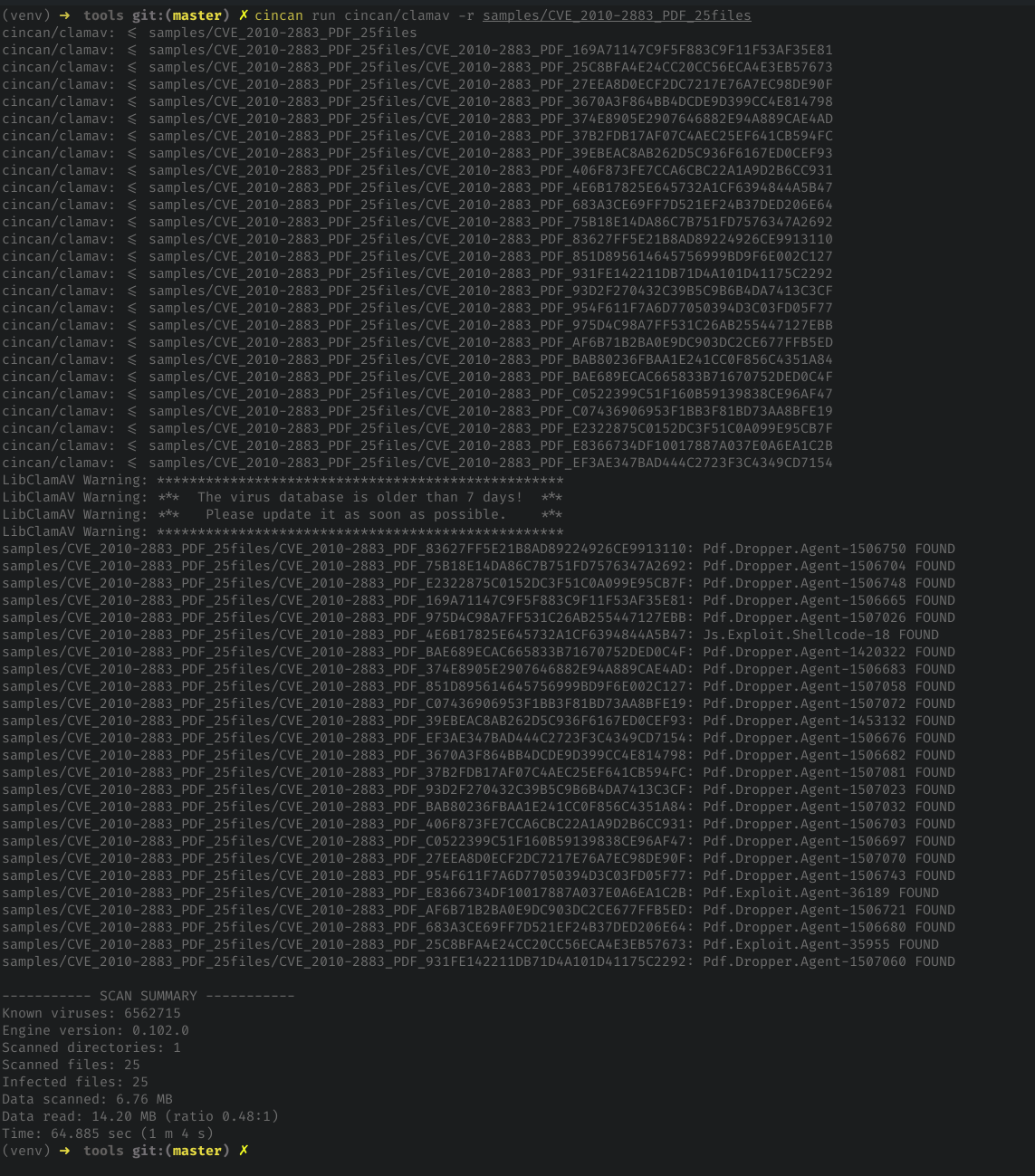
How about if we scan directory full of known malware?
-r flag here specifies recursive scanning.
cincan run cincan/clamav -r samples/CVE_2010-2883_PDF_25files
All of the scanning capabilities are available in the container - with exception of daemon-like running. This requires modification for Dockerfile, if there is for example a case, where daemon should scan for specific shared volume in background.
Database updating
As we are using Docker images, database is only updated during the building phase. However, we can still update it manually.
We need to create container with docker run command and update database with "freshclam" by changing entrypoint:
docker run -it --entrypoint "freshclam" cincan/clamav
Once the update process is finished, we need to commit changes from container into our base image.
Find the latest container with:
$ docker ps -a | grep clamav
02bf4704ce68 cincan/clamav "/bin/sh" 4 minutes ago Exited (0) 7 seconds ago modest_chatelet
cd36c397e137 cincan/clamav "/usr/bin/clamscan -…" 5 minutes ago Exited (0) 5 minutes ago interesting_hermann
And commit database update changes for image:
docker commit --change='ENTRYPOINT ["clamscan"]' 02bf4704ce68 cincan/clamav
Note, that entrypoint should be specified, because we overrided it previously with docker run command!
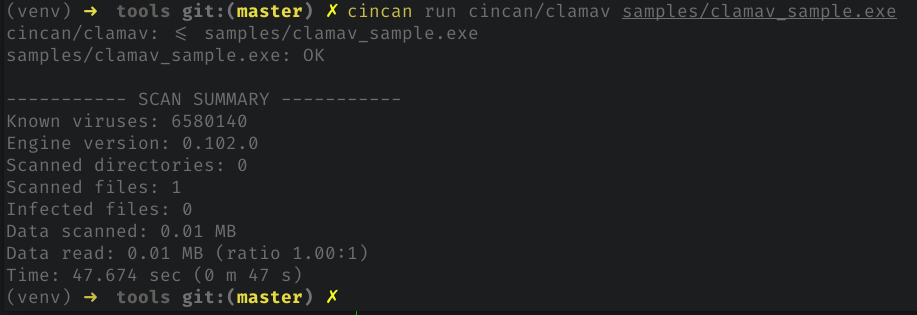
Now, if we run the 'clamscan' again, we won't be seeing "outdated database warnings"... at least for 4 hours.
For Dockerfile and more instructions and many other tools see our tools repository!
[1]: https://www.theregister.co.uk/2001/11/01/powerpuff_girls_catch_funlove_virus/
[2]: https://web.archive.org/web/20080526023945/http://www.sans.edu/resources/securitylab/tomasz_kojm.php
[3]: https://web.archive.org/web/20070216014012/http://www.clamav.net:80/about/