Day 19 - Oletools
Writer: Niklas Saari - OUSPG / University of Oulu
Christmas Eve is getting closer, but the amount of tools is still increasing. This time we have another set of multiple tools - oletools for analysing Microsoft's OLE2 files.
Malicious OLE2 files
Using Microsoft Office's macro-enabled documents for distributing malware is common method. Many might not be aware of macros or about the possibility that these documents can contain them, and what they can actually do.
The first known 'wild' macro virus is known as 'Concept', and it was discovered in 1995. The self-spread property made this virus as most spread virus in 1996 according to Virusbulletin. Since then, existence of malicious Office documents is known wildly.
In todays calendar event, we are taking note for toolset 'oletools' which is directly focused on analysing Microsoft's OLE2 file format (it is used in Word documents for example). We already presented similar tool already earlier, in the 8th day, which is actually using same core: 'olefile' parser-library as dependency, the work of 'oletools' author.
Oletools are providing different kind methods for attempting in identifying malicious documents, and seeing the structure of OLE files in deep level.
'Olefile' - the oleparser and oletools oriented on using it, have been originally developed by Philippe Lagadec.
Big thanks for Philippe Lagadec for developing such tools!
See the homepage of projects over here.
Analysing
In the CinCan project, we have made Docker image from the toolkit, among other tools. For helping with usage of different kind containers - cincan tool wrapper has been created. We are providing some examples how to use these tools with this cincan wrapper, however they are usable with normal Docker commands as well.
There are totally 11 different tools in the kit, whereas two (olebrowse, olemap) are excluded from the container, because they are requiring GUI based dependencies.
Tools are divided into identifying malware: oleid, olevba, MacroRaptor, msodde, pyxswf and oleobj
... and for tools for analysing structure of OLE files: olemeta, oletimes and oledir
Consult project's wikipage for more information.
Simple top level script has been created as user interface, that each of the tools are easily usable from container.
We are using couple of tools as example. First look for olevba, to make simple analysis without arguments. Installation of cincan tool is required. We are using malicious-like document as an example. It can be found from our tools repository.
To make default analysis for document with olevba, run
cincan run cincan/oletools olevba _samples/msoffice/very_suspicious.doc
Which should produce following output:
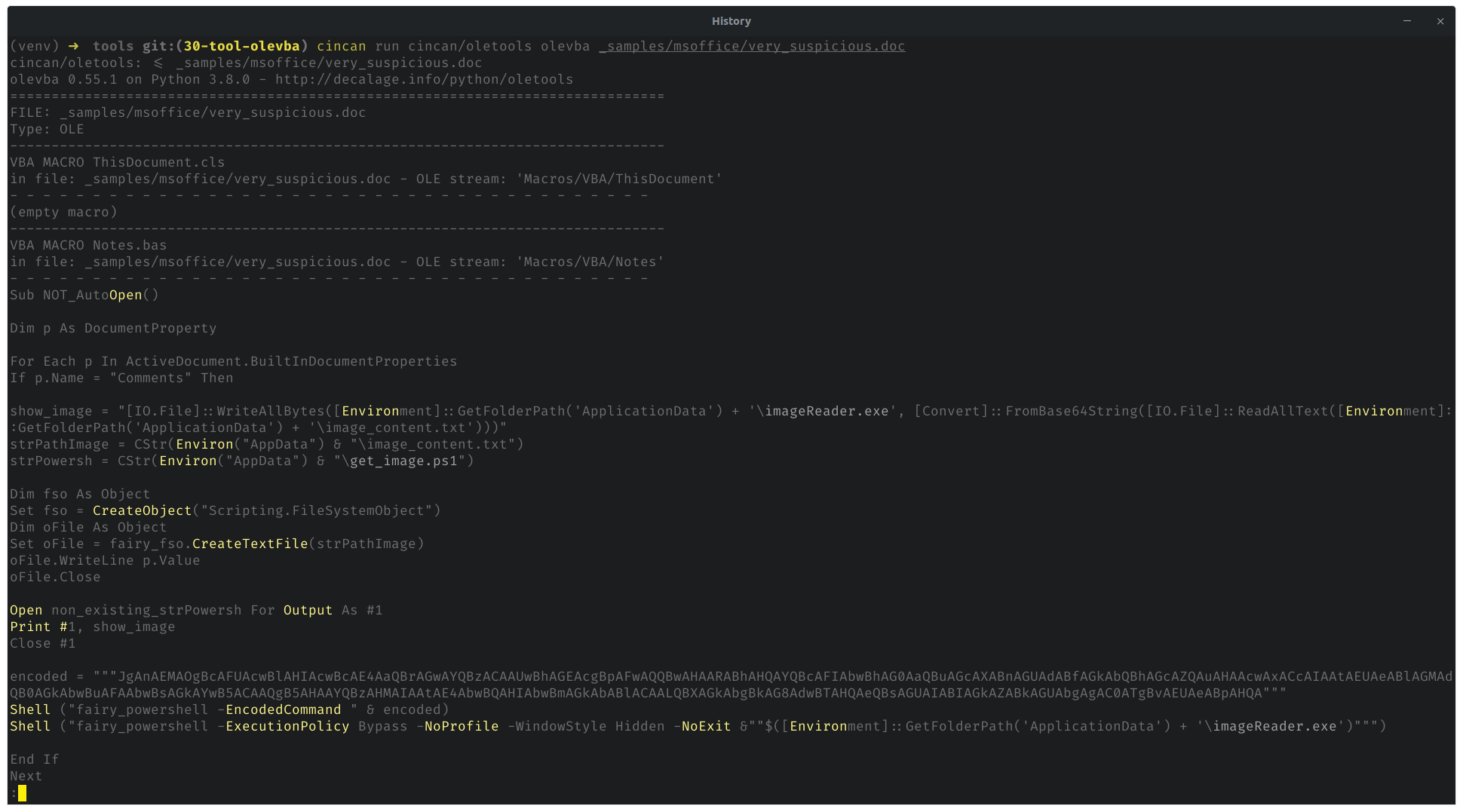
Scrolling down more reveals also interesting section about 'keywords' from the Macros:
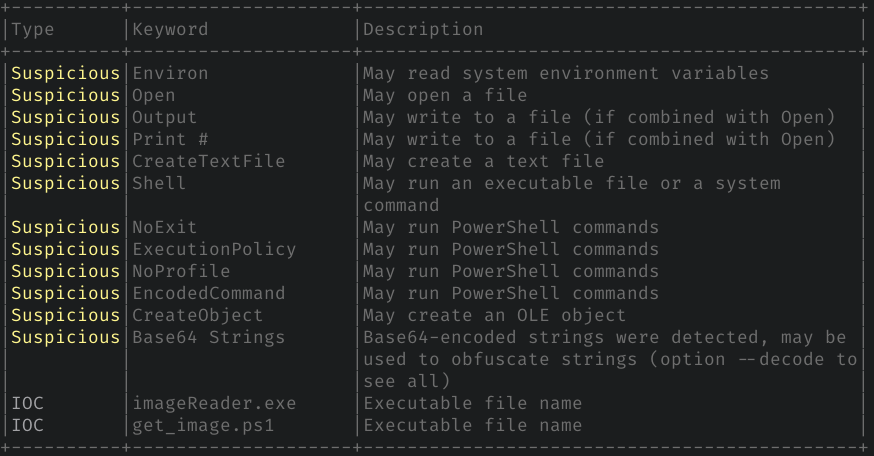
This analysis gives good glance in general, whether document contains macros and what they might do. In this particular document, there is indeed malicious macro which is running PowerShell to install remote malware with embedded base64 encoded payload binary. Olevba is revealing bit of this behavior, without going deep into code by yourself.
As an another example, oledir can be used to show the structure of OLE file:
cincan run cincan/oletools oledir _samples/msoffice/very_suspicious.doc
This produces structured view of the document file.
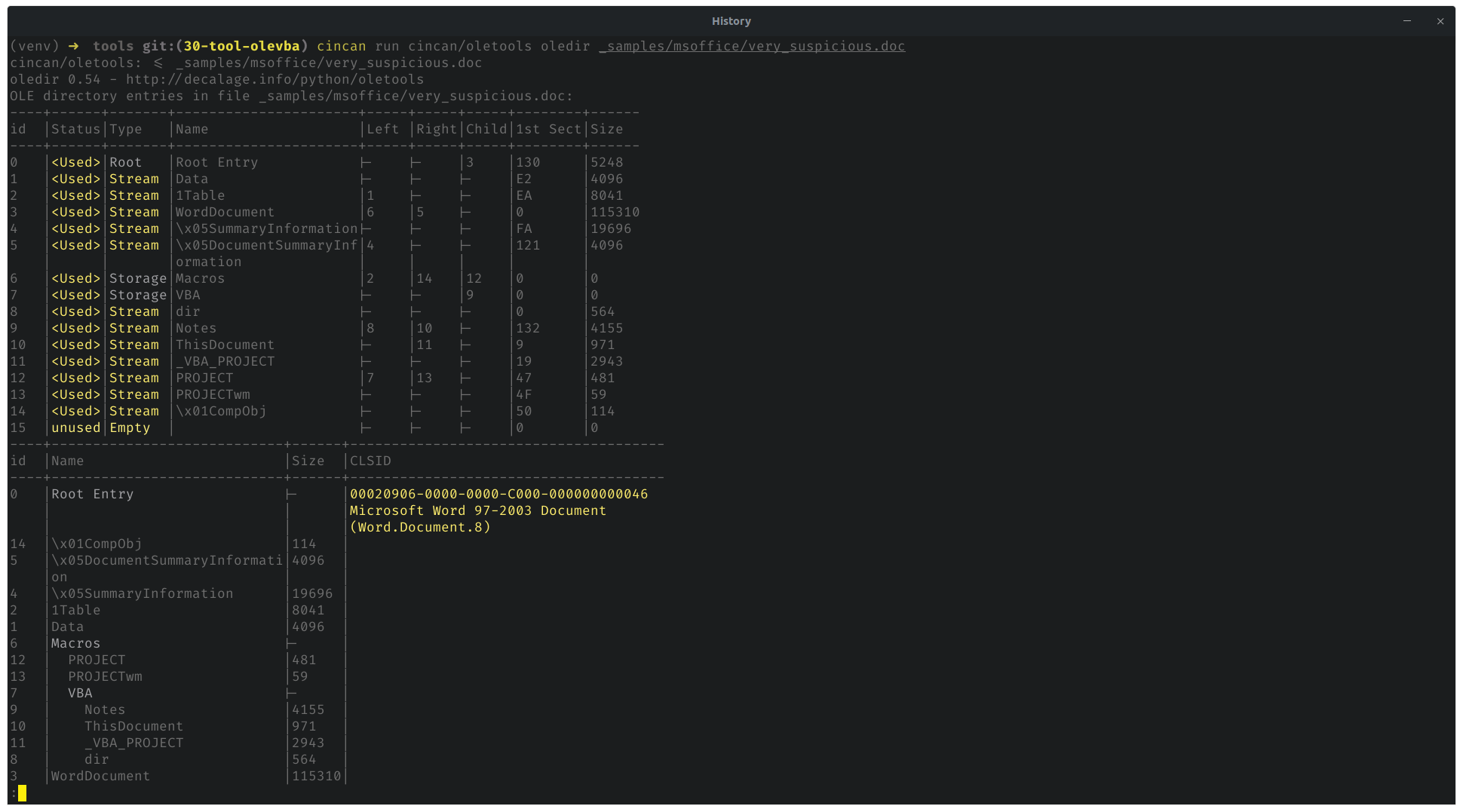
Seems like that summary information is quite big. Might be worth to check the actual content. In this case - that is the place where base64 encoded binary payload is stored.
To see all available tools in container and for further info, just run
cincan run cincan/oletools --help
For Dockerfile and more instructions and many other tools see our tools repository!