Day 21: FireEye Labs Obfuscated String Solver (FLOSS)
Writer: Ville Kalliokoski - OUSPG / University of Oulu
Finding human-readable strings in malware samples is one of the first steps of malware analysis, and for that we have the built-in strings on Linux. But what can you do, when the creators try to obfuscate these? FireEye has created FLOSS just for this: it does everything strings does, but it also tries to automatically deobfuscate the hidden strings.
FLOSS does this by heuristically identifying decoding routines, extracting cross references and arguments for these decoders, then emulating these routines with the extracted arguments. For more information on the theory behind this, you can check FLOSS' documentation on the subject.
Basic usage is identical to strings (example sample can be found in the cincan repository):
$ cincan run cincan/floss _samples/msdos/suspicious_dos_sample.exe
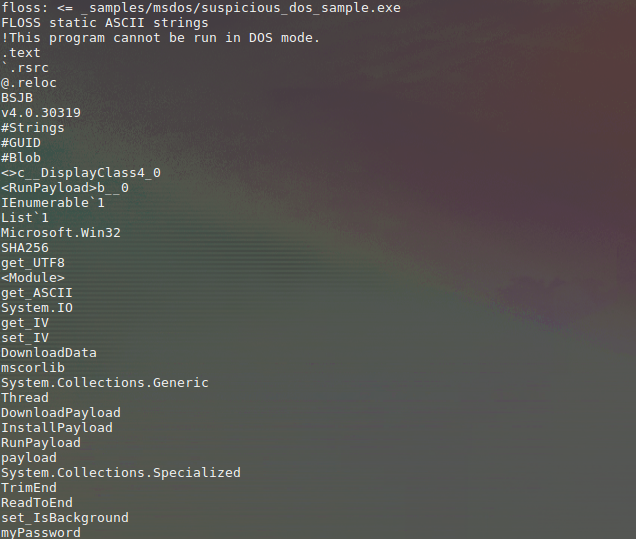
FLOSS also provides a variety of options to aid in the research:
- --no-
-strings: Disable certain type of strings from extraction (available filters: static,decoded,stack) -q, --quiet: Quiet mode-n, --minimum-length: Minimum string length-g, --group: Group decoded strings by decoding routine-f, --functions: Decode strings provided to spesific functions. this is done with using their hex-encoded virtual address:floss -f 0x401000, 0x402000 /path/to/sample--save-workspace: Save the vivisect .viv workspace file to the current directory-m, --show-metainfo: Display basic meta information about the generated vivisect workspace. If used in conjuction with the-foption FLOSS will display meta information about the selected function--no-filter: Do not filter possible false-positives from the deobfuscated strings-i, --ida/ -j, --binja / -r, --radare / --x64dbg: If you want to generate annotation scripts for IDA, Binary Ninja, radare2 or x64dbg database, you can use these flags.-v, --verbose: Verbose mode-d, --debug: Debug mode-l, --list-plugins: List installed plugins used to run heuristics that identify decoding routines-p, --plugins: You can enable only a subset of the plugins by providing a comma-separated list of them to the-pflag-s: For analyzing raw binary files containing shellcode, use the-sswitch. All the above options can also be used when analyzing shellcode.-b, --shellcode_base: Specify a base address for the shellcode-e, --shellcode_ep: Specify an entry point for the shellcode
For more complete usage guide, documentation, source code and more info about FLOSS, check out their repository.
This, and many other dockerized tools can be downloaded from Docker Hub and CinCan project's Gitlab repository.