Day 3 - ILSpy/ilspycmd
Writer: Niklas Saari - OUSPG / University of Oulu
.NET Assemblies and reverse-engineering?
Sometimes there might be a case where we want to make some reverse-engineering and forensics research for binary which was originally created with Microsoft's .NET Framework.
The way how .NET code compiles into binary code differs drastically when compared to traditional C/C++ binaries, and this difference gives us a way to acquire original source code of the binary in somewhat less complicated ways. (With exception of obfuscated binaries.)
.NET code (C#, F#, Visual Basic and so on) compiles mostly into Common Intermediate Language (CIL), which is not direct machine/native code, and just when it is executed by .NET Framework's Common Language Runtime Execution (CLR) engine, it is finally transformed into native code by just-in-time compilation. In .NET Core, this execution engine is called as CoreCLR.
As the binaries are stored in Common Language Infrastructure (CLI) assemblies, which are usually better known as .NET assemblies, the reversing progress is different for these kind of binaries, and is known to be easy for unobfuscated ones.
Getting the work done
ILSpy is one of the most known decompiler engines and browsers for the .NET family assemblies. It supports direct code compilation and whole-project decompilation to C#. Many additional front-ends have been implemented for it, such as dnSpy.
ILSpy was originally created by Daniel Grunwald and David Srbecký in 2011 as response to Red Gate's announcement that the popular .NET decompiler "Reflector" would be changed to be commercial product, non-free. Other contributors are the rest of the SharpDevelop team and many other open-source contributors. Big thanks to them!
See the project in the GitHub
In the CinCan project, we have dockerized many analysis tools, and ILSpy is one of them, as console version.
Tool named as cincan is created to run these different kind of dockerized tools, and here we have some examples about using it with ILSpy. Installation of this tool is enough - it downloads docker containers automatically when running selected tool.
We are using sample file which is provided in CinCan's tool repository with the ILSpy. There are also additional instructions and visible Dockerfile.
Note about sample file:, it is not malicious, but code re-presents common malicious behavior.
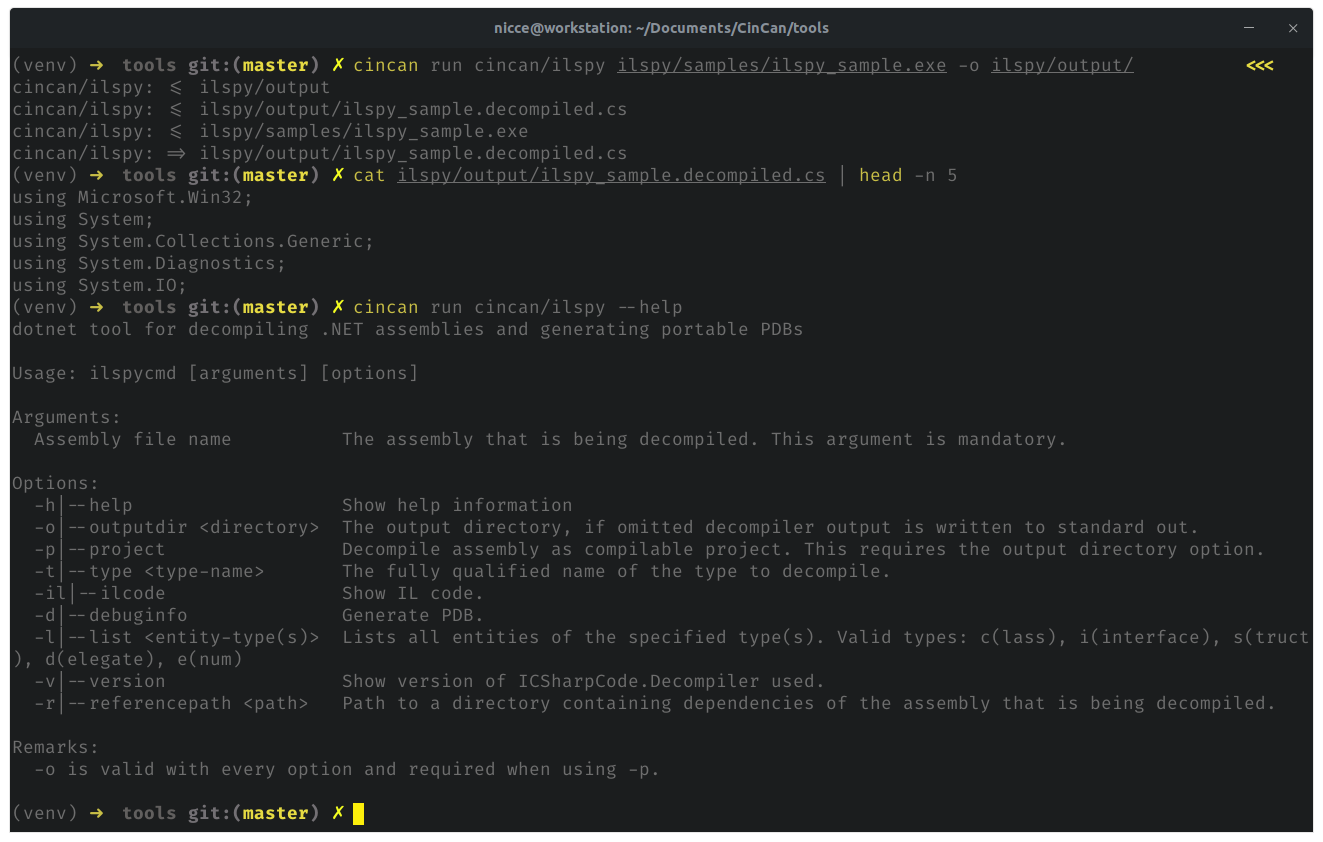
To simply decompile binary without extra parameters, following command can be executed. Note, that output directory should be created beforehand.
cincan run cincan/ilspy ilspy/samples/ilspy_sample.exe -o ilspy/output/
This generates single C# file as decompiled output.
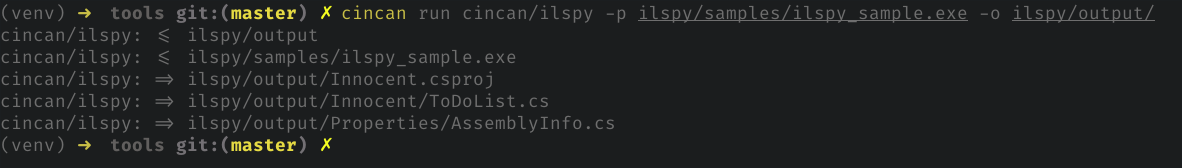
To compile binary as project, we just add single parameter for command:
cincan run cincan/ilspy -p ilspy/samples/ilspy_sample.exe -o ilspy/output/
Cincan tool detects this time the produced project output structure.
All of the functionality of ILSpy console version is fully working, these were just couple of examples.
Containers can be used without cincan tool as well, here are docker run alternatives for above commands:
docker run --rm -v <LOCALVOLUMEDIR>/samples:/samples -t cincan/ilspy /samples/ilspy_sample.exe -o /samples/output/
And
docker run --rm -v <LOCALVOLUMEDIR>/samples:/samples -t cincan/ilspy -p /samples/ilspy_sample.exe -o /samples/output/
Take a look for many other tools in CinCan’s Gitlab repository!