Investigating IoCs in malware using cincan command
Writer: Vesa Vertainen, Project Engineer, JAMK University of Applied Sciences
IoCs, indicators of compromise, are artifacts like hashes, URLs, IPs or email addresses that indicate an intrusion. In this blog we are going to investigate IoCs in a ransomware using CINCAN tools.
Pay, or else…
Ransomware typically encrypts files on a victim’s computer and demands ransom to be paid in order to let the victim access the files again. The current pandemic has also inspired new ransomware. According to INTERPOL many hospitals have become targets, and these threat actors are “looking to make profit at the expense of sick patients”.
In this blog we analyze an older case of ransomware, called WannaCry, also known as WannaCrypt or WannaCryptor. WannaCry was a ransomware, that caused over 300 000 computers to be infected in May 2017. It demanded a few hundred US dollars in bitcoins, in order to decrypt victim’s files. WannaCry did not although have a system to identify who had paid the money, so there was no way getting the computer decrypted via paying the ransom. WannaCry was stopped, as a researcher noticed that the malware called a certain unregistered domain. The researcher registered that domain, and for his surprise, unintentionally activated a kill switch, shutting down WannaCry.
The quest for IoCs
Using CINCAN's tool ioc_strings, the “kill switch” domain is easy to notice. Ioc_strings is a tool similar to Linux’s strings, but it tries to identify IoC’s and only output those probably meaningful strings.
To analyze WannaCry with ioc_strings using the cincan command, we type:
cincan run cincan/ioc_strings Win32.Wannacry.exe
Ioc_strings outputs IoC types in JSON format. The first line is interesting. This is the domain name that was working as a kind of a kill switch:
{"ioc": "http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com", "ioc_types": ["url"]}
Threat intelligence feeds
With another tool that was created by the Cincan project, feature_extractor, we can analyze the IoCs that were composed with ioc_strings to iocs.json file:
Running cincan run cincan/feature_extractor the first time creates the configuration files needed in the analysis. Then by modifying the active_analyzers file, we select which threat intelligence feeds are used for the analysis:
#AbuseIPDB/AbuseIPDB
#Censys/Censys
#GoogleSafebrowsing/GoogleSafebrowsing
#MISPWarningLists2/MISPWarningLists2
PhishTank/PhishTank_CheckURL
#DShield/DShield_lookup
#GreyNoise/GreyNoise
#OTXQuery/OTXQuery
#Shodan/Shodan_DNSResolve
#Shodan/Shodan_Host
#Shodan/Shodan_Host_History
#Shodan/Shodan_InfoDomain
#Shodan/Shodan_ReverseDNS
#Shodan/Shodan_Search
#Threatcrowd/Threatcrowd
#EmergingThreats/EmergingThreats_DomainInfo
VirusTotal/VirusTotal_GetReport
#VirusTotal/VirusTotal_Scan
#CinCanTools/CinCanTools
In this case, we use PhishTank and VirusTotal feeds. Next, to activate them, we run:
cincan run cincan/feature_extractor -–injsonl iocs.json -–path ./
Then, we fill API keys to this API.json file:
{
"PhishTank": {
"key": ""
},
"VirusTotal": {
"key": ""
}
Then, to run feature_extractor using the API keys, we type again:
cincan run cincan/feature_extractor –injsonl iocs.json –path ./
This creates the features.html report from the selected feeds:
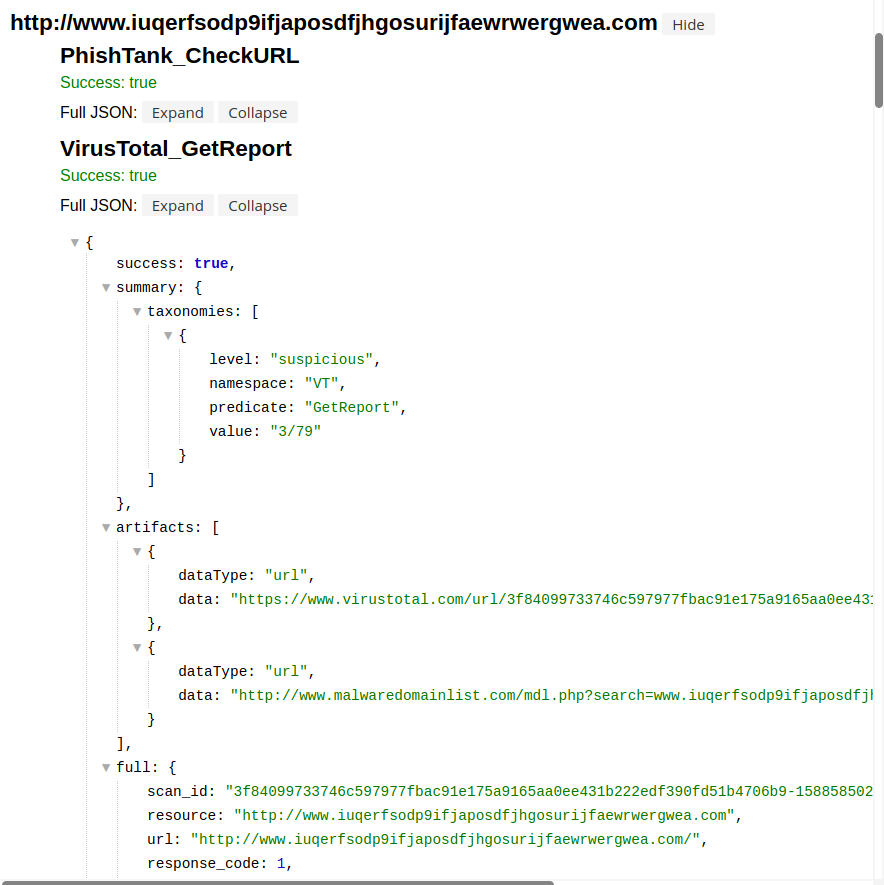
Inspecting the VirusTotal part of the report shows that only 3 of the 79 intelligence feeds consider the domain suspicious. This WannaCry sinkhole domain is currently run by Kryptos Logic, the company that stopped WannaCry's first wave.
Click here to view the full feature_extractor results html.
Hints to protect your system from ransomware:
- keep your software always up to date
- make backups of your essential files (online / offline)
- be careful (don’t click suspicious email attachments / links)