Day 11 - Peframe
Writer: Ville Kalliokoski - OUSPG / University of Oulu
Behind the 11th window in the CinCan advent calendar we have peframe, currently maintained by Gianni 'guelfoweb' Amato.
Peframe is an open source tool for static analysis of portable executable files, a file format for executables, object code, DLLs, font files and others for Windows. It is ubiquitous in Windows, and can be found everywhere from your everyday Windows executables to Office macros and device drivers. Peframe can be used to look for packers, digital signatures, anti-forensic techniques, macros and other relevant information in digital forensics.
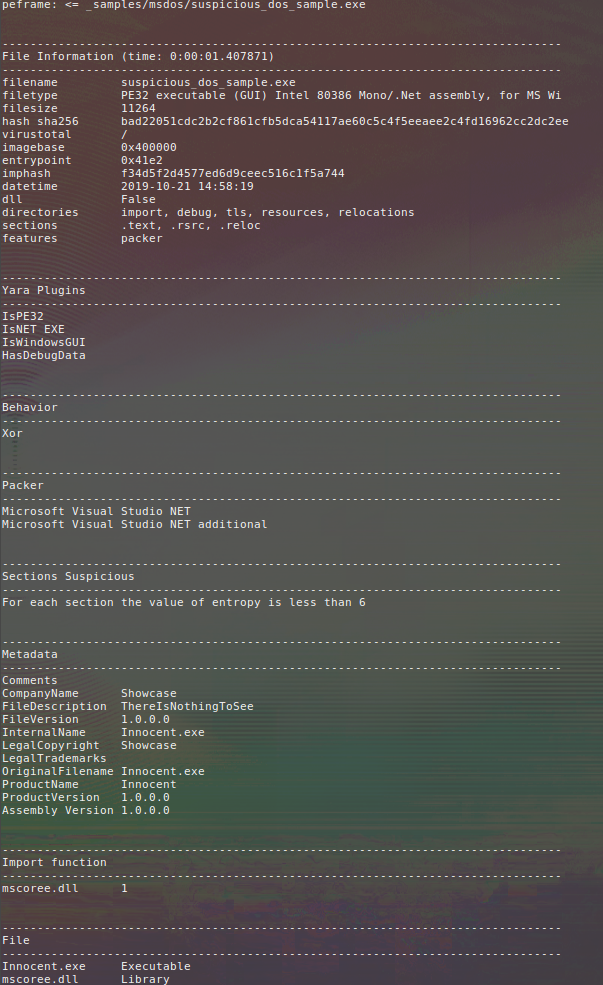
Basic usage is simple (_samples folder is in the root of cincan repository):
$ cincan run peframe _samples/msdos/suspicious_dos_sample.exe
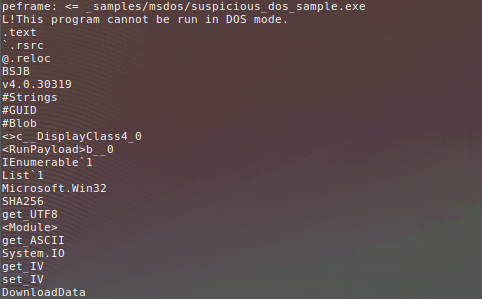
You can also search for strings or xored strings:
$ cincan run peframe -s samples/peframe_sample.exe
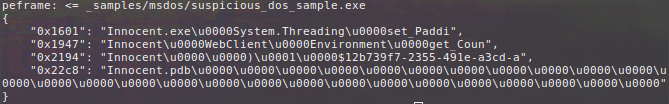
$ cincan run peframe -x Innocent _samples/msdos/suspicious_dos_sample.exe
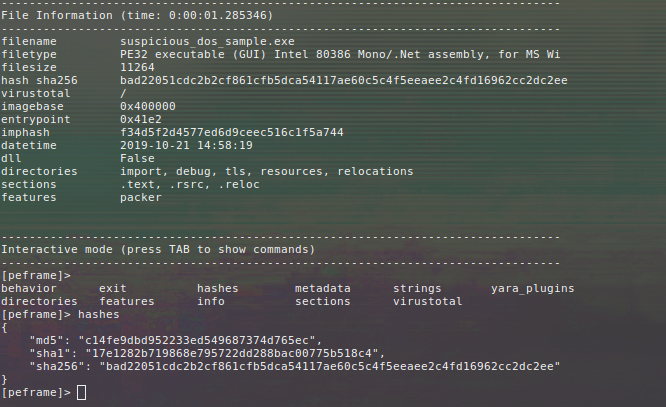
Peframe also offers an interactive mode (note that CinCan tool doesn't currently support this):
$ docker run --rm -it -v "$(pwd)"/_samples:/samples cincan/peframe -i /samples/msdos/suspicious_dos_sample.exe
The CinCan tool, dockerized peframe and many more tools can be found from CinCan’s Gitlab repository, and the Docker hub.